


The key to success in protecting a company is to be aware of the risk and implement a correct strategy.
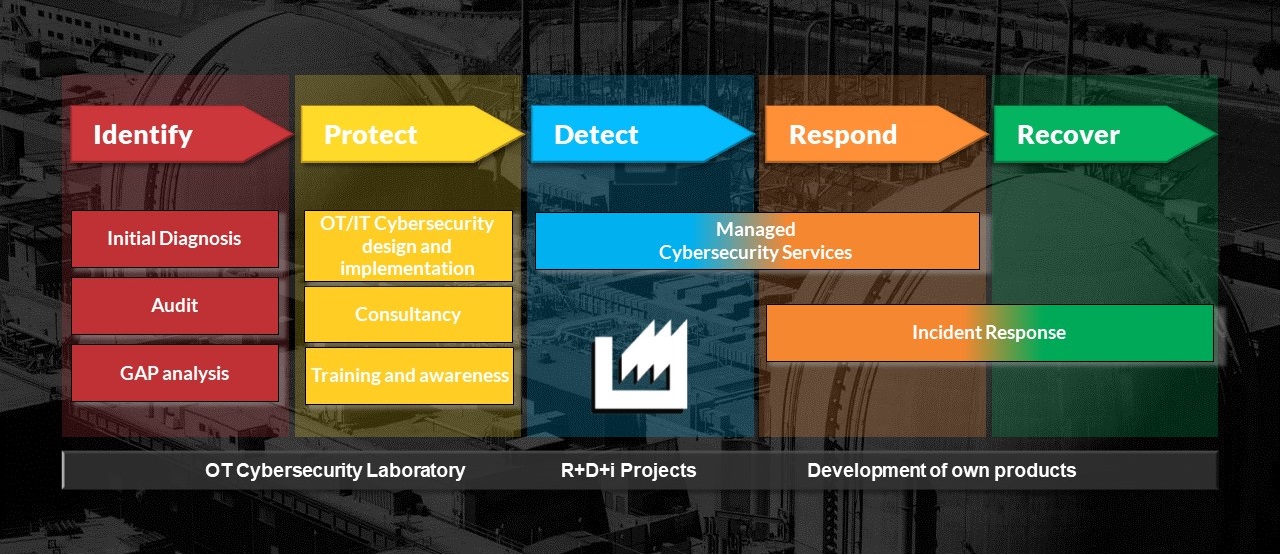
The phases to follow to have a good strategy in cybersecurity are identify, protect, detect, respond and recover the information
Our cybersecurity services provide the necessary value to the business to determine the strategy necessary for the organization.
These services allow you to manage the complete life cycle of an industrial cybersecurity system.
- Identify: organizational understanding to manage the CS risk of systems, assets, data and capabilities.
- Protect: implement the appropriate safeguards to guarantee the delivery of critical infrastructure services.
- Detect: activities to identify the occurrence of a cybersecurity event.
- Respond: activities to take action with respect to a detected event.
- Recover: activities to maintain resilience plans and restore capabilities or services that were seen affected.
Identify is to obtain a real image of the cybersecurity status of your industrial installation.
Obtaining three basic data: a list of assets, industrial communications protocols used, and data traffic between industrial equipment.
It allows us to understand your organization and your installation to manage the cybersecurity risk of systems, assets, data and capabilities.
This information allows us to perform a correct IT / OT segmentation and to model a new secure architecture.
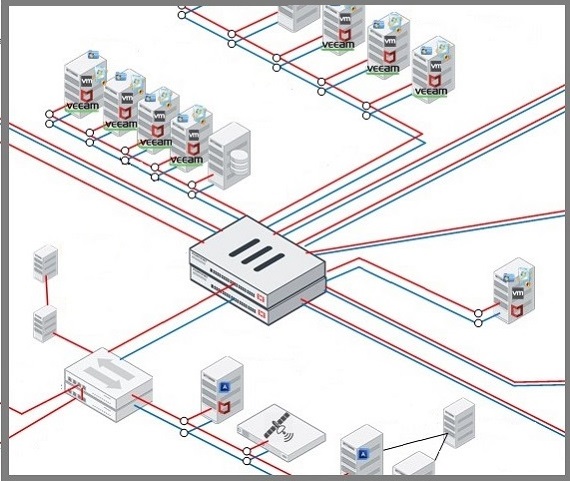
Assessment of cybersecurity risk status of industrial installations through traffic analysis, device configuration, documentation and procedure review.
The work is carried out using Titanium’s own technologies and passive, non-disruptive techniques.

Test your company’s response against an external and internal attack using the techniques of a real attacker (ethical hacking, vulnerability analysis, internal and external intrusion test, social engineering).

IEC 62443, ISO 27001, NIS / UE 2016/1148 preliminary audit implementation.
Protect is deploying the countermeasures and security safeguards recommended in the identification phase, implementing the new secure architectures.
The deployment of measures adapted to each industrial need, allows reducing the level of risk of the installation, which complemented by a system of cybersecurity policies decreases your level of exposure.
People are also part of the security of the installation, therefore, training and awareness is a vital milestone for the success of the project.
And as a complement, our consulting service that allows you to guide the client in case of any doubt.

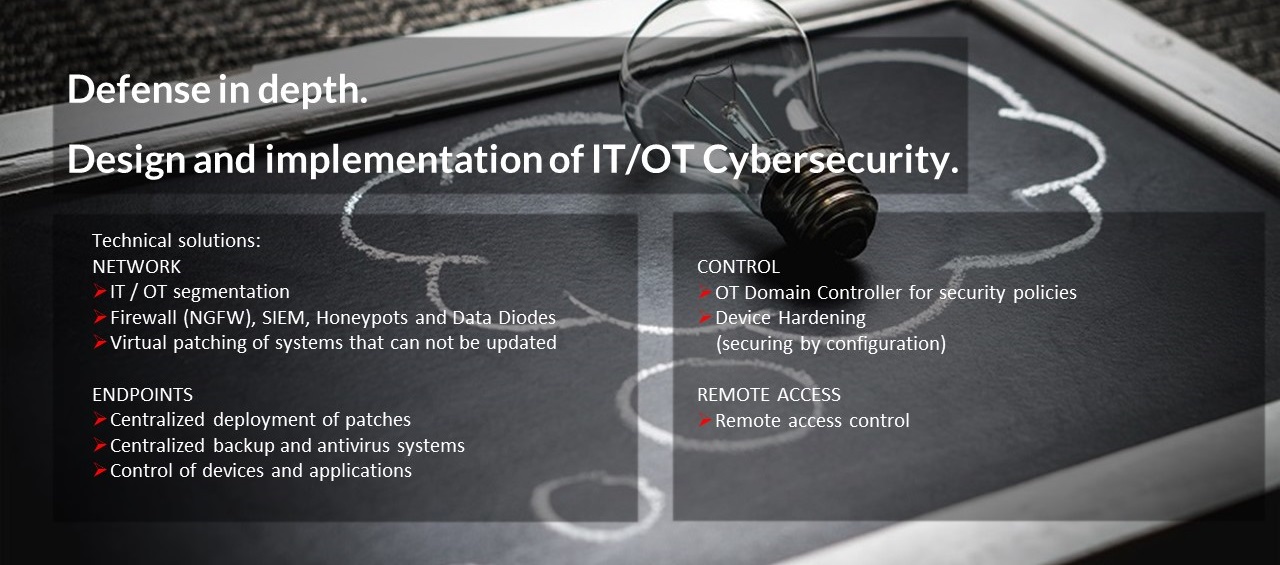
We design and implement secure architectures based on international standards, through IT / OT segmentation and deployment of specific solutions for industrial control system protection.

Technical consulting services, systems and products pre-certification and regulatory body development.
Our goal is to ACCOMPANY industries in their secure control system process implementation and maintenance.

We provide staff awareness courses targeting your IT / OT personnel and provide targeted phishing campaigns and cybersecurity solutions training.
Detecting to be able to identify the occurrence of an incident is vital, in order to be able to take action quickly.
Followed by an answer, taking the appropriate measures and in time, it allows to contain the incident in the shortest possible time.
And, if necessary, to recover, restoring the capacities and services affected by the event.
A security system is useless if the occurrence of an incident is not detected and identified.
When an incident occurs, time is a critical factor, if not acted on time, the damage will be greater.
Many times the customer has no time or knowledge to manage them properly.
In these cases, these functions are covered with our support and monitoring services.
Monitoring, intrusion detection, incident and vulnerability management and solutions maintenance.

We assist with incident management, create contingency and disaster recovery plans and perform forensic analysis.
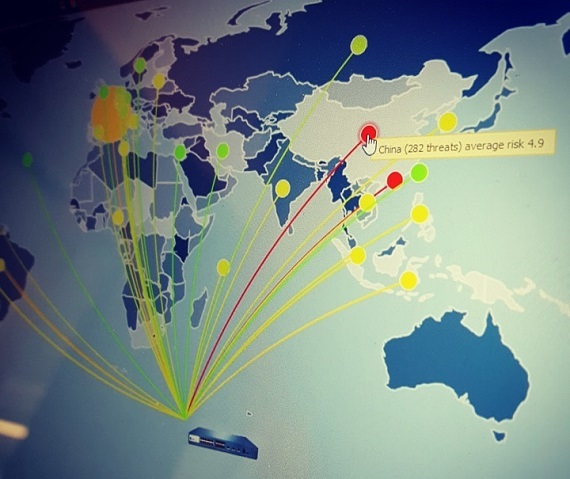
We offer a continuous monitoring and management of security events, 24x7x365.
The laboratory is a controlled environment for testing, development and evaluation (own or third-party) of products and systems in realistic way, simulating a complete industrial ecosystem.

We guide and accompany industrial companies to comply with regulations and standards.